Paper 2 - Category
The basic parts of a desktop computer are the computer case, monitor, keyboard, mouse, and power cord. Each part plays an important role whenever you use a computer.

The power supply unit in a computer converts the power from the wall outlet to the type of power needed by the computer. It sends power through the cables to the motherboard and other components.
If you decide to open the computer case and take a look, make sure to unplug the computer first. Before touching the inside of the computer, you should touch a grounded metal object (or a metal part of the computer casing) to discharge any static buildup. Static electricity can be transmitted through the computer circuits and ruin them.
An input device is any hardware component that allows users to enter data and instructions (programs, commands, and user responses) into a computer. Depending on the application and your particular requirements, the input device selected may vary. The following pages discuss a variety of input devices. Storage devices, such as disk drives, serve as both input and output devices.

Keyboard

Mouse

Trackball
A trackball is a stationary pointing device with a ball on its top or side (Figure 5-9). The ball in most trackballs is about the size of a Ping-Pong ball. To move the pointer using a trackball, you rotate the ball with your thumb, fingers, or the palm of your hand. In addition to the ball, a trackball usually has one or more buttons that work just like mouse buttons.

Touchpad
A touchpad is a small, flat, rectangular pointing device that is sensitive to pressure and motion (Figure 5-10). To move the pointer using a touchpad, slide your fingertip across the surface of the pad. Some touchpads have one or more buttons around the edge of the pad that work like mouse buttons. On most touchpads, you also can tap the pad’s surface to imitate mouse operations such as clicking. Touchpads are found most often on notebook computers, including netbooks and many Tablet PCs.

Touch screens
A touch screen is a touch-sensitive display device. Touch screens that recognize multiple points of contact at the same time are known as multi-touch. Users can interact with touch screens by touching areas of the screen. Because touch screens require a lot of arm or hand movements, you do not enter large amounts of data using a touch screen. Instead, you touch words, pictures, numbers, letters, or locations identified on the screen. Some touch screens also respond to finger motions such as sliding your finger to drag an object or pinching your fingers to zoom in or out. The latest version of the Windows operating system provides increased support for computers with touch screens. Support for touch screen makes it easier for users to interact with the operating system.

Digital Cameras
a digital camera is a mobile device that allows users to take pictures and store the photographed images digitally, instead of on traditional film. While many digital cameras look like a traditional camera, many mobile devices such as smart phones, PDAs, and portable media players often have a built-in digital camera. Mobile users such as real estate agents, insurance agents, general contractors, and photojournalists use digital cameras so that they immediately can view photographed images on the camera. Home and business users have digital cameras to save the expense of film developing, duplication, and postage.
Biometric Devices
Biometrics is the technology of authenticating a person’s identity by verifying a personal characteristic. Biometric devices grant users access to programs, systems, or rooms by analyzing some biometric identifier. A biometric identifier is a physiological (related to physical or chemical activities in the body) or behavioral characteristic. Examples include fingerprints, hand geometry, facial features, voice, signatures, and eye patterns.
A biometric device translates a personal char acteristic (the input) into a digital code that is compared with a digital code stored in the computer. If the digital code in the computer does not match the personal characteristic’s code, the computer denies access to the individual. The most widely used biometric device today is a fingerprint reader. A fingerprint reader, or scanner, captures curves and indentations of a fingerprint. The reader can be set up to perform different functions for different fingers; for example, one finger starts a program and another finger shuts down the computer.

Output Devices
Output is data that has been processed into a useful form. That is, computers process data (input) into information (output). The form of output varies, depending on the hardware and software being used and the requirements of the user. Monitors, traditional notebook computers, netbooks, Tablet PCs, portable media players, smart phones, digital cameras, and other mobile devices have screens that allow users to view documents, Web sites, e-mail messages, photos, videos, and movies. Many printers enable users to print color documents and photos. Through the computer’s speakers, headphones, or earbuds, users listen to sounds, music, and voice messages.

An LCD monitor is a desktop monitor that uses a liquid crystal display to produce images. These monitors produce sharp, flicker-free images. LCD monitors have a small footprint; that is, they do not take up much desk space. For additional space savings, some LCD monitors are wall mountable. LCD monitors are available in a variety of sizes, with the more common being 19, 20, 22, 24, 26, 27, and 30 inches — some are 45 or 65 inches. Most are widescreen, which are wider than they are tall. You measure a monitor the same way you measure a television, that is, diagonally from one corner to the other. Determining which size monitor to purchase depends on your intended use. A large monitor allows you to view more information on the screen at once, but usually is more expensive.
Printers
A printer is an output device that produces text and graphics on a physical medium such as paper. Printed information, called hard copy, exists physically and is a more permanent form of output than that presented on a display device (soft copy).
Non impact Printers
A nonimpact printer forms characters and graphics on a piece of paper without actually striking the paper. Some spray ink, while others use heat or pressure to create images. Commonly used nonimpact printers are ink-jet printers, photo printers, laser printers, thermal printers, mobile printers, label and postage printers, plotters, and large-format printers.
An ink-jet printer is a type of nonimpact printer that forms characters and graphics by spraying tiny drops of liquid ink onto a piece of paper. Ink-jet printers have become a popular type of color printer for use in the home.
A laser printer is a high-speed, high-quality nonimpact printer (Figure 6-18). Laser printers are available in both black-and-white and color models. A laser printer for personal computers ordinarily uses individual 81/2 3 11-inch sheets of paper stored in one or more removable trays that slide in the printer case. Some laser printers have built-in trays that accom modate dif ferent sizes of paper, while others require separate trays for letter- and legal-sized paper. Most laser printers have a manual feed slot where you can insert individual sheets and envelopes. Laser printers print text and graphics in high-quality resolutions, usually 1200 dpi for black-and-white printers and up to 2400 dpi for color printers.
A multifunction peripheral (MFP), also called an all-in-one device, is a single device that looks like a printer or a copy machine but provides the functionality of a printer, scanner, copy machine, and perhaps a fax machine (Figure 6-20). A fax machine is a device that codes and encodes documents so that they can be transmitted over telephone lines. The documents can contain text, drawings or photos, or can be handwritten. The features of these devices vary. For example, some use color ink-jet printer technology, while others include a black-and-white or color laser printer. Small offices and home office (SOHO) users have multifunction peripherals because these devices require less space than having a separate printer, scanner, copy machine, and fax machine. Another advantage of these devices is they are significantly less expensive than if you purchase each device separately. If the device breaks down, however, you lose all four functions, which is the primary disadvantage.
An audio output device is a component of a computer that produces music, speech, or other sounds, such as beeps. Three commonly used audio output devices are speakers, headphones, and earbuds. Most personal computers and mobile devices have a small internal speaker that usually emits only low-quality sound. Thus, many users attach surround sound speakers or speaker systems to their com puters, including game consoles and mobile devices, to generate higher-quality sounds for playing games, interacting with multimedia presentations, listening to music, and viewing movies.
A data projector is a device that takes the text and images displaying on a computer screen and projects them on a larger screen so that an audience can see the image clearly. For example, many classrooms use data projectors so that all students easily can see an instructor’s presentation on the screen.
An interactive whiteboard is a touch-sensitive device, resembling a dry-erase board, that displays the image on a connected computer screen. A presenter controls the computer program by clicking a remote control, touching the whiteboard, drawing on or erasing the whiteboard with a special digital pen and eraser, or writing on a special tablet. Notes written on the interactive whiteboard can be saved directly on the computer. Interactive whiteboards are used frequently in classrooms as a teaching tool.
Storage holds data, instructions, and information for future use. Every computer stores system software and application software. To start up, a computer locates an operating system (system software) in storage, usually a hard disk, and loads it into memory (RAM). When a user issues a command to start application software, such as a word processing program or a Web browser, the operating system locates the program in storage, such as on a hard disk or optical disc, and loads it into memory (RAM).
Hard drive

The hard drive is the data center of the computer. This is where the software is installed, and it's also where your documents and other files are stored. The hard drive is long-term storage, which means the data is still saved even if you turn the computer off or unplug it.
When you run a program or open a file, the computer copies some of the data from the hard drive onto the RAM so that it can access the data more easily. When you save a file, the data is copied back to the hard drive. The faster the hard drive is, the faster your computer can start up and load programs.
Most hard drives are hard disk drives, which store data on a magnetic platter. Some computers now use solid-state drives (also called flash hard drives). These are faster and more durable than hard disk drives, but they are also more expensive.
A USB flash drive is basically a small, removable flash hard drive that plugs into a USB port. These are a convenient way to bring your files with you and open them on a different computer.
If you're using Windows, you can view information about your computer's RAM and processor speed without opening up your computer. Just go to the Control Panel (in the Start menu) and click System and Security. In Mac OS X, you can view this information by clicking the Apple icon and selecting About This Mac.
An external hard disk, is a separate freestanding hard disk that connects with a cable to a USB port or FireWire port on the system unit or communicates wirelessly. As with the internal hard disk, the entire hard disk is enclosed in an airtight, sealed case. External hard disks have storage capacities of up to 4 TB and more. Some external hard disk units include multiple hard disks that you can use for different purposes, if desired. A removable hard disk is a hard disk that you insert and remove from a drive. Sometimes the drive is built in the system unit. Others are external devices that connect with a cable to a USB port or FireWire port on the system unit.
Memory cards enable mobile users easily to transport digital photos, music, or files to and from mobile devices and computers or other devices. Common types of memory cards include CompactFlash (CF), Secure Digital (SD), Secure Digital High Capacity (SDHC), microSD, micro SDHC, xD Picture Card, Memory Stick, and Memory Stick Micro (M2).
;
An optical disc is a type of storage media that consists of a flat, round, portable disc made of metal, plastic, and lacquer that is written and read by a laser. (The spelling, disk, is used for magnetic and flash memory media, and disc is used for optical media.) Optical discs used in personal computers are 4.75 inches in diameter and less than one- twentieth of an inch thick. Smaller computers, game consoles, and mobile devices, however, often use mini discs that have a diameter of 3 inches or less
RAM is your system's short-term memory. Whenever your computer performs calculations, it temporarily stores the data in the RAM until it is needed.
This short-term memory disappears when the computer is turned off. If you're working on a document, spreadsheet, or other type of file, you'll need to save it to avoid losing it. When you save a file, the data is written to the hard drive, which acts as long-term storage.
RAM is measured in megabytes (MB) or gigabytes (GB). The more RAM you have, the more things your computer can do at the same time. If you don't have enough RAM, you may notice that your computer is sluggish when you have several programs open. Because of this, many people add extra RAM to their computers to improve performance.
A bit is the smallest unit of data in computer processing. A byte is a group of eight bits. A megabyte contains about one million bytes, and a gigabyte is about one billion bytes.

The Central Processing Unit (CPU), also called a processor, is located inside the computer case on the motherboard. It is sometimes called the brain of the computer, and its job is to carry out commands. Whenever you press a key, click the mouse, or start an application, you're sending instructions to the CPU.
The CPU is generally a 2-inch ceramic square with a silicon chip located inside. The chip is usually about the size of a thumbnail. The CPU fits into the motherboard's CPU socket, which is covered by the heat sink, an object that absorbs heat from the CPU.
A processor's speed is measured in megahertz (MHz), or millions of instructions per second, and gigahertz (GHz), or billions of instructions per second. A faster processor can execute instructions more quickly. However, the actual speed of the computer depends on the speed of many different components - not just the processor.
There are many processor manufacturers for personal computers, but the most well-known ones are Intel and AMD.

The motherboard is the computer's main circuit board. It's a thin plate that holds the CPU, memory, connectors for the hard drive and optical drives, expansion cards to control the video and audio, as well as connections to your computer's ports (such as the USB ports). The motherboard connects directly or indirectly to every part of the computer.

Most computers have expansion slots on the motherboard that allow you to add various types of expansion cards. These are sometimes called PCI (Peripheral Component Interconnect) cards. You may never have to add any PCI cards, as most motherboards have built-in video, sound, network, and other capabilities. However, if you want to boost the performance of your computer or update the capabilities of an older computer, you can always add one or more cards. Below are some of the most common types of expansion cards:

The video card is responsible for what you see on the monitor. Most computers have a GPU (Graphics Processing Unit) built into the motherboard, instead of having a separate video card. If you like playing graphics-intense games on the computer, you can add a faster video card to one of the expansion slots to get better performance.
The sound card, also called an audio card, is responsible for what you hear in the speakers or headphones. Most motherboards have integrated sound, but you can upgrade to a dedicated sound card for higher quality sound.
The network card allows your computer to communicate over a network and access the internet. It can either connect with an Ethernet cable or through a wireless connection (often called Wi-Fi). Many motherboards have built-in network connections, and a network card can also be added to an expansion slot.

Bluetooth is a technology for wireless communication over short distances. It's often used in computers to communicate with wireless keyboards, mice, and printers. It's often built into the motherboard or included in a wireless network card. For computers that don't have Bluetooth, a USB adapter (called a dongle) can be purchased.
The computer goes blank before the Word document was saved. The browser window freezes for no reason. You can't hear anything from your speakers.
Most people have at one time or another experienced a computer problem like the situations just described, and if you haven't, chances are you will at some point. When a problem occurs, don't panic! Instead, work your way through some basic troubleshooting techniques and try to solve the problem.

There are many devices, parts, cords, and connections on a computer, which means that there are many possible problems that could arise. In addition, your computer uses a variety of software, which can also cause problems. However, no matter what the problem is, you can use the following tips to help you find a solution:
Most of the time, problems can be fixed by using simple troubleshooting techniques, such as closing and re-opening the program. It's important to try these simple solutions before resorting to more extreme measures. If the problem still isn't fixed, you can then try other troubleshooting techniques, such as reinstalling the software.


If you still haven't found a solution to your problem, you may need to ask someone else for help. Try searching the web for the problem that you're having, as other people may have had similar problems. Also, if you have a friend or family member who knows a lot about computers, they may be able to help you.
Keep in mind that most computer problems have simple solutions, although it may take some time to find them. For very difficult problems, a more drastic solution may be required, such as reformatting your hard drive, reinstalling programs, or reinstalling your operating system. If you're not a computer expert, it's possible that you could make the situation worse, so it's best to consult a professional if you think a drastic solution is needed.
What is an Operating System / software?
An operating system is the most important software that runs on a computer. It manages the computer's memory, processes, and all of its software and hardware. It also allows you to communicate with the computer without knowing how to speak the computer's "language." Without an operating system, a computer is useless.
You've probably heard the phrase boot your computer, but do you know what that means? Booting is the process that occurs when you press the power button to turn your computer on. During this process (which may take a minute or two), the computer does several things:
Once the operating system has started up, it manages all of the software and hardware on the computer. Most of the time, there are many different programs running at the same time, and they all need to access your computer's Central Processing Unit (CPU), memory, and storage. The operating system coordinates all of this to make sure that each program gets what it needs. Without the operating system, the software wouldn't even be able to talk to the hardware, and the computer would be useless.
Operating systems usually come preloaded on any computer that you buy. Most people use the operating system that comes with their computer, but it is possible to upgrade or even change operating systems.
The three most common operating systems for personal computers are Microsoft Windows, Apple Mac OS X, and Linux.

Modern operating systems use a Graphical User Interface, or GUI (pronounced "gooey"). A GUI lets you use your mouse to click on icons, buttons, and menus, and everything is clearly displayed on the screen using a combination of graphics and text.
Each operating system's GUI has a different look and feel, so if you switch to a different operating system it may seem unfamiliar at first. However, modern operating systems are designed to be easy to use, and most of the basic principles are the same.
Before GUIs, computers had a command-line interface, which meant the user had to type every single command to the computer, and the computer would only display text.
Microsoft created the Windows operating system in the mid-1980s. Over the years, there have been many different versions of Windows, but the most recent ones are Windows 8 (released in 2012), Windows 7 (2009), and Windows Vista (2007). Windows comes preloaded on most new PCs, which helps to make it the most popular operating system in the world.
If you're buying a new computer or upgrading to a newer version of Windows, you can choose from several different editions of Windows, such as Home Premium, Professional, and Ultimate. You may need to do some research to decide which edition is right for you.
Mac OS is a line of operating systems created by Apple Inc. It comes preloaded on all new Macintosh computers, or Macs. All of the recent versions are known as Mac OS X (pronounced Mac O-S Ten), and their specific version names are Mountain Lion (released in 2012), Lion (2011), and Snow Leopard (2009). Apple also offers a version called Mac OS X Server, which is designed to be run on servers.
According to StatCounter Global Stats, Mac OS X users account for 7.5% of the operating systems market as of January 2013 - much lower than the percentage of Windows users (over 90%). One reason for this is that Apple computers tend to be more expensive. However, many people prefer the look and feel of Mac OS X.
Linux (pronounce LINN-ux) is a family of open source operating systems, which means that they can be modified and distributed by anyone around the world. This is very different from proprietary software like Windows, which can only be modified by the company that owns it (Microsoft). The advantages of Linux are that it is free, and there are many different distributions (or versions) that you can choose from. Each distribution has a different look and feel, and the most popular ones include Ubuntu, Mint, and Fedora.
Linux is named after Linus Torvalds, who created the Linux kernel in 1991. The kernel is the computer code that is the central part of an operating system.
The operating systems that we've been talking about were designed to run on desktop or laptop computers. Mobile devices such as phones, tablet computers, and mp3 players are very different from desktop and laptop computers, so they run operating systems that are designed specifically for mobile devices. Examples of mobile operating systems include Apple iOS, Windows Phone, and Google Android.
Operating Systems for mobile devices generally aren't as fully-featured as those made for desktop or laptop computers, and they aren't able to run all of the same software. However, you can still do a lot of things with them, such as watching movies, browsing the internet, managing your calendar, playing games, and more.
With the proper software, a computer is a
valuable tool. Software allows users to create
letters, memos, reports, and other documents;
develop multimedia presentations; design Web
pages and diagrams; draw and alter images; record
and enhance audio and video clips; prepare and
file taxes; play single player or multiplayer games;
compose e-mail messages and instant messages;
and much more. To accomplish these and many
other tasks, users work with application software.
Application software consists of programs
designed to make users more productive and/or
assist them with personal tasks. Application
software has a variety of uses:
1. To make business activities more efficient
2. To assist with graphics and multimedia projects
3. To support home, personal, and educational
tasks
4. To facilitate communications
Open source software is software provided for use, modification, and redistribution. This software has no restrictions from the copyright holder regarding modification of the software’s internal instructions and its redistribution. Open source software usually can be downloaded from the Internet, often at no cost.
Communication software is an application or program designed to pass information from one system to another. Communication software is used to provide remote access to systems and exchange files and messages in text, audio and/or video formats between different computers or users.
A utility program, also called a utility, is a type of system software that allows a user to perform maintenance-type tasks, usually related to managing a computer, its devices, or its programs. Most operating systems include several built-in utility programs. Functions provided by utility programs include the following: managing files, searching for files, viewing images, uninstalling programs, cleaning up disks, defragmenting disks, backing up files and disks, setting up screen savers, securing a computer from unauthorized access, protecting against viruses, removing spyware and adware, filtering Internet content, compressing files, playing media files, burning optical discs, and maintaining a personal computer.
Disk Cleanup
Disk Defragmenter
Uninstaller
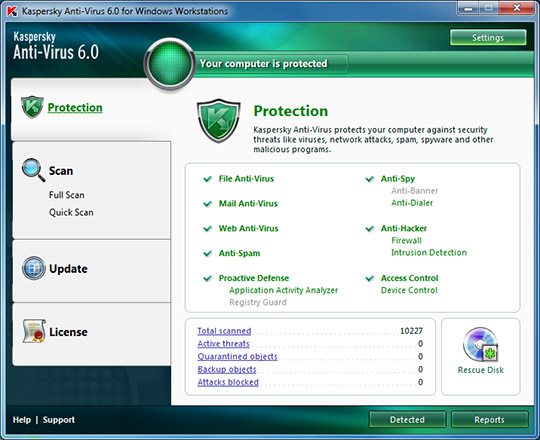
Anti -virus
The term, computer virus, describes a potentially damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without the user’s knowledge or permission. Once the virus is in a computer, it can spread throughout and may damage your files and operating system.
Signs of virus infections
An unusual message or image is displayed on the computer screen
• An unusual sound or music plays randomly
• The available memory is less than what should be available
• A program or file suddenly is missing
• An unknown program or fi le mysteriously appears
• The size of a file changes without explanation
• A file becomes corrupted
• A program or file does not work properly
• System properties change
• The computer operates much slower than usual
Viruses are just one type of malicious software.
Malware (short for malicious software) is software
that acts without a user’s knowledge and deliberately
alters the computer’s operations. In addition
to viruses, worms and Trojan horses are malware.
A worm copies itself
repeatedly, for example, in memory or over a
network, using up system resources and possibly
shutting down the system. A Trojan horse
(named after the Greek myth) hides within or
looks like a legitimate program such as a screen
saver. A certain condition or action usually triggers
the Trojan horse. Unlike a virus or worm,
a Trojan horse does not replicate itself to other
computers. Currently, more than one million
known threats to your computer exist.To protect a computer from virus attacks,
users should install an antivirus program and
update it frequently. An antivirus program protects
a computer against viruses by identifying
and removing any computer viruses found in
memory, on storage media, or on incoming
files. Most antivirus programs also protect
against worms and Trojan horses.
File Compression
A file compression utility shrinks the size of a file(s). A compressed file takes up less storage space than the original file. Compressing files frees up room on the storage media and improve system performance. Attaching a compressed file to an e-mail message, for example, reduces the time needed for file transmission. Uploading and downloading compressed files to and from the Internet reduces the file transmission timeCompressed files, sometimes called zipped files, usually have a .zip extension. When you receive or download a compressed file, you must uncompress it. To uncompress, or unzip, a file, you restore it to its original form. Some operating systems such as Windows include file compression and uncompression capabilities. Two popular stand-alone file compression utilities are PKZIP and WinZip.
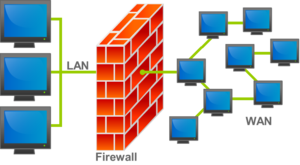
LAN
A local area network (LAN) is a network that connects computers and devices in a limited geographical area such as a home, school computer laboratory, office building, or closely positioned group of buildings. Each computer or device on the network, called a node, often shares resources such as printers, large hard disks, and programs. Often, the nodes are connected via cables.
WLAN
A wireless LAN (WLAN) is a LAN that uses no physical wires. Computers and devices that access a wireless LAN must have built-in wireless capability or the appropriate wireless network card, USB network adapter, ExpressCard module, PC Card, or flash card. Very often, a WLAN communicates with a wired LAN for access to its resources, such as software, hardware, and the Internet.
WAN
A wide area network (WAN) is a network that covers a large geographic area (such as a city, country, or the world) using a communications channel that combines many types of media such as telephone lines, cables, and radio waves. A WAN can be one large network or can consist of two or more LANs connected together. The Internet is the world’s largest WAN.
Dial-Up Lines
A dial-up line is a temporary connection that uses one or more analog telephone lines for communications. A dial-up connection is not permanent. Using a dial-up line to connect computers costs no more than making a regular telephone call.
Dedicated Lines
A dedicated line is a type of always-on connection that is established between two communications devices (unlike a dial-up line where the connection is reestablished each time it is used). The quality and consistency of the connection on a dedicated line are better than a dial-up line because dedicated lines provide a constant connection. Businesses often use dedicated lines to connect geographically distant offices. Dedicated lines can be either analog or digital. Digital lines increasingly are connecting home and business users to networks around the globe because they transmit data and information at faster rates than analog lines.
ISDN Lines - dedicated line
For the small business and home user, an ISDN line provides faster transfer rates than dial-up telephone lines. Not as widely used today as in the past, ISDN (Integrated Services Digital Network) is a set of standards for digital transmission of data over standard copper telephone lines. With ISDN, the same telephone line that could carry only one computer signal now can carry three or more signals at once through the same line, using a technique called multiplexing.
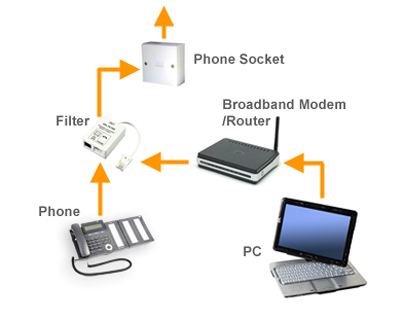
DSL- dedicated line
DSL is a popular digital line alternative for the small business or home user. DSL (Digital Subscriber Line) transmits at fast speeds on existing standard copper telephone wiring. Some DSL installations include a dial tone, providing users with both voice and data communications. These DSL installations often require that filters be installed to reduce noise interference when voice communications share the same line. ADSL is one of the more popular types of DSLs. ADSL (asymmetric digital subscriber line) is a type of DSL that supports faster transfer rates when receiving data (the downstream rate) than when sending data (the upstream rate). ADSL is ideal for Internet access because most users download more information from the Internet than they upload.
Dial-Up Modems - dial up line
A dial-up modem is a communications device that can convert digital signals to analog signals and analog signals to digital signals, so that data can travel along an analog telephone line. Recall that an analog signal consists of a continuous electrical wave, and a digital signal consists of individual electrical pulses that represent bits grouped together into bytes. For example, a dial-up modem connected to a sending computer converts the computer’s digital signals into analog signals. The analog signals then can travel over a standard telephone line. At the receiving end, if necessary, another dial-up modem converts the analog signals back into digital signals that a receiving computer can process. A dial-up modem usually is in the form of an adapter card that you insert in an expansion slot on a computer’s motherboard. One end of a standard telephone cord attaches to a port on the modem card and the other end plugs into a telephone outlet. Devices other than computers also use modems. A stand-alone fax machine, for example, has a modem that converts a scanned digitized image into an analog signal that is sent to a recipient’s fax machine.
Digital Modems: ISDN, DSL, and Cable
A digital modem is a communications device that sends and receives data and information to and from a digital line. Three types of digital modems are ISDN modems, DSL modems, and cable modems. These modems typically include built-in Wi-Fi connectivity. An ISDN modem sends digital data and information from a computer to an ISDN line and receives digital data and information from an ISDN line. A DSL modem sends digital data and information from a computer to a DSL line and receives digital data and information from a DSL line. ISDN and DSL modems usually are external devices, in which one end connects to the telephone line and the other end connects to a port on the system unit.
Wireless Modems
Some mobile users have a wireless modem that uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smart phone, or other mobile device. Wireless modems, which have an external or built-in antenna, are available as USB flash drives, ExpressCard modules, PC Cards, and memory cards. Some smart phones also can function as a wireless modem when connected with a special cable to a personal computer.
Network Cards
A network card, sometimes called a network interface card (NIC pronounced nick), is a communications device that enables a computer or device that does not have built-in networking capability to access a network. The network card coordinates the transmission and receipt of data, instructions, and information to and from the computer or device containing the network card. Network cards are available in a variety of styles. A network card for a desktop computer is an adapter card that has a port to which a cable connects. A network card for mobile computers and devices is in the form of a USB network adapter, ExpressCard module, PC Card, or a memory card. Network cards that provide wireless data transmission also are available. This type of card, called a wireless network card, often has an antenna. Sometimes the antenna is detachable, allowing the user to position it in a location with the best signal strength. Users also can install an amplifier to increase and/or stabilize the signal strength. Some network cards include support for both wired and wireless networks. A network card follows the guidelines of a particular network communications standard, such as Ethernet or token ring. An Ethernet card is the most common type of network card. Ethernet cards may support multiple speeds.
Wireless Access Points
A wireless access point is a central communications device that allows computers and devices to transfer data wirelessly among themselves or to transfer data wirelessly to a wired network. Wireless access points have high-quality antennas for optimal signals. For the best signal, some manufacturers suggest positioning the wireless access point at the highest possible location and the use of an amplifier.
Routers
A router is a communications device that connects multiple computers or other routers together and transmits data to its correct destination on a network. A router can be used on any size of network. On the largest scale, routers along the Internet backbone forward data packets to their destination using the fastest available path. For smaller business and home networks, a router allows multiple computers to share a single high-speed Internet connection such as through a cable modem or DSL modem. These routers connect from 2 to 250 computers. To prevent unauthorized users from accessing files and computers, many routers are protected by a built-in firewall, called a hardware firewall. Some also have built-in antivirus protection. Routers also support wireless communications, eliminating the need for a separate wireless access point in a wireless network. If the network has a separate wireless access point, it connects to the router via a cable. Some routers also include additional functionality such as including a built-in print server. Today’s routers or combination wireless access point/routers are easy to configure and secure against unauthorized access.
Hubs and Switches
Today, thousands of computer networks exist, ranging from small networks operated by home users to global networks operated by numerous telecommunications firms. Inter connecting these many types of networks requires various types of communications devices. A hub or switch is a device that provides a central point for cables in a network (Figure 9-32). Larger networks typically use a hub, while smaller networks use a switch. Some hubs and/or switches include routers. That is, the hub or switch receives data from many directions and then forwards it to one or more destinations.
Types
On a client/server network, one or more computers act as a server, and the other computers on the network request ser vices from the server (Figure 9-13). A server, sometimes called a host computer, controls access to the hardware, software, and other resources on the network and provides a centralized storage area for programs, data, and information. The clients are other computers and mobile devices on the network that rely on the server for its resources. For example, a server might store a database of customers. Clients on the network (company employees) access the customer database on the server.
One type of peer-to-peer network is a simple, inexpensive network that typically connects fewer than 10 computers. Each computer, called a peer, has equal responsibilities and capabilities, sharing hardware (such as a printer), data, or information with other computers on the peer-to-peer network (Figure 9-14). Each computer stores files on its own storage devices. Thus, each computer on the network contains both the server operating system and application software. All computers on the network share any peripheral device(s) attached to any computer. For example, one computer may have a laser printer and a scanner, while another has an ink-jet printer and an external hard disk.
A network topology refers to the layout of the computers and devices in a communications network. Three commonly used network topologies are star, bus, and ring. Most networks, including the Internet, use combinations of these topologies.
Star Network
Star Network On a star network, all of the computers and devices (nodes) on the network connect to a central device, thus forming a star. Two types of devices that provide a common central connection point for nodes on the network are a hub and a switch. All data that transfers from one node to another passes through the hub or switch. Star networks are fairly easy to install and maintain. Nodes can be added to and removed from the network with little or no disruption to the network. On a star network, if one node fails, only that node is affected. The other nodes continue to operate normally. If the hub or switch fails, however, the entire network is inoperable until the device is repaired. Most large star networks, therefore, keep backup hubs or switches available in case the primary one fails.
Bus Network
A bus network consists of a single central cable, to which all computers and other devices connect. The bus is the physical cable that connects the computers; and other devices. The bus in a bus network transmits data, instructions, and information in both directions. When a sending device transmits data, the address of the receiving device is included with the transmission so that the data is routed to the appropriate receiving device. Bus networks are popular on LANs because they are inexpensive and easy to install. One advantage of the bus network is that computers and other devices can be attached and detached at any point on the bus without disturbing the rest of the network. Another advantage is that failure of one device usually does not affect the rest of the bus network. The greatest risk to a bus network is that the bus itself might become inoperable. If that happens, the network remains inoperative until the bus is back in working order.
Ring Network
On a ring network, a cable forms a closed loop (ring) with all computers and devices arranged along the ring. Data transmitted on a ring network travels from device to device around the entire ring, in one direction. When a computer or device sends data, the data travels to each computer on the ring until it reaches its destination. If a computer or device on a ring network fails, the entire network potentially could stop functioning. A ring network can span a larger distance than a bus network, but it is more difficult to install. The ring topology primarily is used for LANs, but also is used in WANs.
Network Cards
A network card, sometimes called a network interface card (NIC pronounced nick), is a communications device that enables a computer or device that does not have built-in networking capability to access a network. The network card coordinates the transmission and receipt of data, instructions, and information to and from the computer or device containing the network card. Network cards are available in a variety of styles. A network card for a desktop computer is an adapter card that has a port to which a cable connects. A network card for mobile computers and devices is in the form of a USB network adapter, ExpressCard module, PC Card, or a memory card.
Hubs and switches
Today, thousands of computer networks exist, ranging from small networks operated by home users to global networks operated by numerous telecommunications firms. Inter connecting these many types of networks requires various types of communications devices. A hub or switch is a device that provides a central point for cables in a network. Larger networks typically use a hub, while smaller networks use a switch. Some hubs and/or switches include routers. That is, the hub or switch receives data from many directions and then forwards it to one or more destinations.
An ISP (Internet service provider) is a regional or national access provider. Internet is through an Internet service provider (ISP). The providers are already connected to the Internet and provide a path or connection for individuals to access the Internet. Your school or university most likely provides you with free access to the Internet either through its local area networks or possibly through a dial-up or telephone connection. There are also some companies that offer free Internet access. The most widely used commercial Internet service providers are national and wireless providers. They provide access through standard telephone or cable connections. Users can access the Internet from almost anywhere within the country for a standard fee without incurring long-distance telephone charges. Wireless service providers offer Internet connections for computers with wireless modems and a wide array of wireless devices.
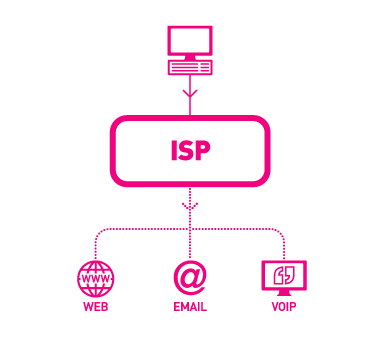
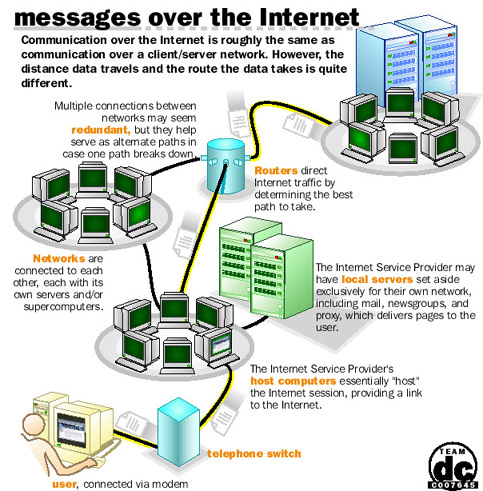
Browsers are programs that provide access to Web resources. This software connects you to remote computers, opens and transfers files, displays text and images, and provides in one tool an uncomplicated interface to the Internet and Web documents. Browsers allow you to explore, or to surf, the Web by easily moving from one Web site to another. Four wellknown browsers are Mozilla Firefox, Apple Safari, Microsoft Internet Explorer, and Google Chrome.
A Web browser, or browser, is application software that allows users to access and view Web pages or access Web 2.0 programs. To browse the Web, you need a computer or mobile device that is connected to the Internet and has a Web browser. The more widely used Web browsers for personal computers are Internet Explorer, Firefox, Opera, Safari, and Google Chrome. With an Internet connection established, you start a Web browser. The browser retrieves and displays a starting Web page, sometimes called the browser’s home page.

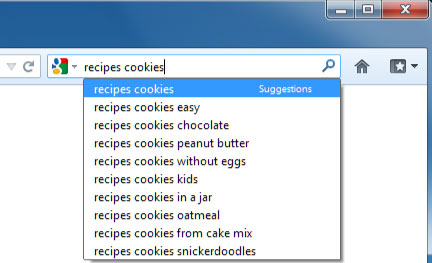
With billions of web pages on the World Wide Web, how can you find exactly what you're looking for? By using a search engine.
Search engines are specialized web sites that help you find what you're looking for on the Web. All you have to do is type in one or more keywords, and the search engine will look for matching web sites from all over the Web.
In this lesson, you'll learn the basics of using a search engine, as well as some techniques you can use to get better search results.
There are numerous search engines out there, but the most popular ones are Google, Yahoo, and Bing. Each one has its own unique features, but the process of doing a search is very similar on each.
Many browsers have a built-in search bar, located to the right of the address bar. To do a search, just type what you're looking for (known as the search terms) in the search bar, and then press Enter. Your browser will then take you to the search engine's web site to show you the search results, which is a list of all of the web sites that contain your search terms.
Many browsers allow you to add to or change the search engines used by the search bar.
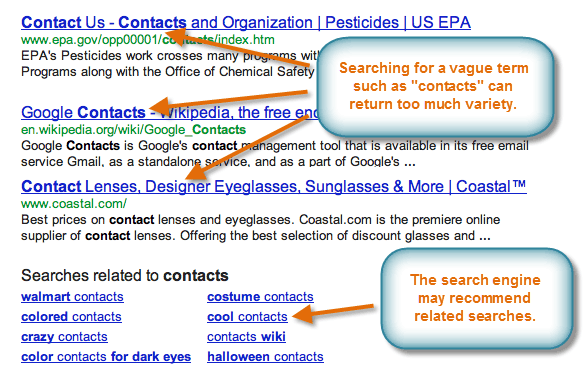
After you do a search, glance over the first page of search results. Did it return what you are looking for, or is it just a lot of unnecessary "junk"?
If your search results don't seem very good, you may need to try different search terms. Remember, the search engine can't read your mind; it just looks for matching words. For example, if you just search for the word polish, the search engine doesn't know whether you're looking for shoe polish or a history of the Polish language!
You could improve your search results by searching for shoe polish. However, that still may return a wide variety of web sites, such as:
To get the best results, ask yourself: What exactly am I looking for? Specific terms usually return better results.
A search engine will often recommend related searches that may be more specific than the search terms you used. Related searches are usually listed at the bottom of the page. Bing also lists them to the left of the search results.
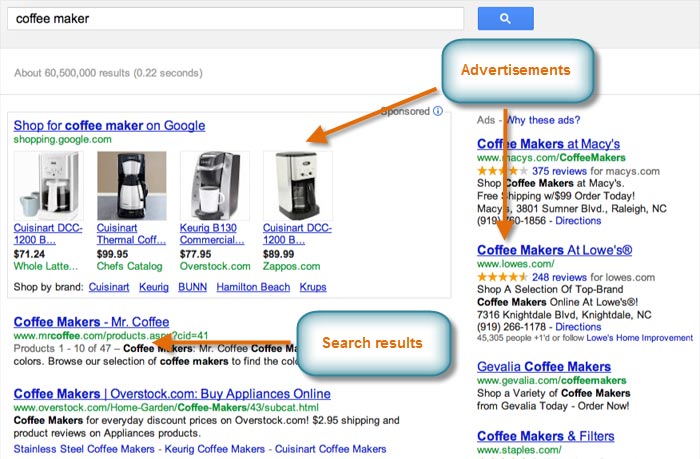
Search engines may include advertisements along with the search results. These ads are picked by the search engine based on your search terms, and they look a lot like the actual search results. While they may be useful in some cases, it's usually more effective to focus on the "regular" search results.
Google puts its ads at the top and to the right of the search results.
As you gain experience with search engines, you'll be able to do better and better searches, which means it will become quicker and easier to find what you are looking for. Here are a few tips for improving your searches:
Search engines are specialized programs that assist you in locating information on the Web and the Internet. To find information, you go to a search service’s Web site and use its search engine. Yahoo’s search engine. This search engine, like most others, provides two different search approaches.
Keyword search: In a keyword search, you enter a keyword or phrase reflecting the information you want.
Directory search: Most search engines also provide a directory or list of categories or topics such as Autos, Finance, and Games. In a directory search, you select a category or topic that fits the information that you want. Another list of subtopics related to the topic you selected appears. You select the subtopic that best relates to your topic and another subtopic list appears.
Content Evaluation
Search engines are excellent tools to locate information on the Web. Be careful, however, how you use the information you find. Unlike most published material found in newspapers, journals, and textbooks, not all the information you find on the Web has been subjected to strict guidelines to ensure accuracy. In fact, anyone can publish content on the Web. Many sites, such as Wikipedia.com, allow anyone to post new material, sometimes anonymously and without critical evaluation. To learn how you can publish on the Web, visit our Web site at www.computing-2012.com and enter the keyword blog.
To evaluate the accuracy of information you find on the Web, consider
the following:
• Authority. Is the author an expert in the subject area? Is the site an official site
for the information presented, or is the site an individual’s personal Web site?
• Accuracy. Has the information been critically reviewed for correctness
prior to posting on the Web? Does the Web site provide a method to report
inaccurate information to the author?
• Objectivity. Is the information factually reported or does the author have
a bias? Does the author appear to have a personal agenda aimed at convincing
or changing the reader’s opinion?
• Currency. Is the information up to date? Does the site specify the date
when the site was updated?
List of some common search Engines
Yahoo
Google
Aardvark.co.za
Bing
The amount of data, instructions, and information that can travel over a communications channel sometimes is called the bandwidth. The higher the bandwidth, the more the channel transmits. For example, a router has more bandwidth than a dial-up modem.
Broadband media transmit multiple signals simultaneously. In many cases, download transfer rates of broadband are faster than its upload transfer rates. Home and business users today opt for broadband Internet access because of the fast transfer rates.
Hotspot

A hotspot is any location where Wi-Fi network access (usually Internet access) is made publicly available. You can often find hotspots in airports, hotels, coffee shops, and other places where business people tend to congregate. Hotspots are considered a valuable productivity tool for business travelers and other frequent users of network services.
Cyber or Internet cafe
An internet café or cybercafé is a place which provides internet access to the public, usually for a fee. Cybercafés are usually located in areas with high population such as schools, colleges and in towns.

Home & Business
As a homeowner (or renter), you likely have several options for how to connect to the Internet. The connection method you choose affects how a home network must be set up to support Internet connection sharing. Each Internet network connection alternative is described here.
DSL is one of the most prevalent forms of Internet connection. DSL provides high-speed networking over ordinary phone lines using digital modems. DSL connection sharing can be easily achieved with either wired or wireless broadband routers.
Most home networks employ Internet Connection Sharing (ICS) solutions with dial up Internet. Dial up routers are difficult to find, expensive, and generally do not perform well given such a slow Internet pipe.
Wireless Internet can also be used at home using 3G technology via usb modem.
Businesses wil make use of ADSL, faster connection to enhance the services of the business.
Wireless Internet enables wireless connectivity to the Internet via radio waves rather than wires on a person's home computer, laptop, smartphone or similar mobile device. Wireless Internet can be accessed directly through providers like AT&T, Verizon, T-Mobile, Boingo and Clearwire. While most wireless Internet options lack the high speed of landline broadband Internet connections such as cable and DSL, newer wireless Internet technologies like EV-DO and WiMAX are narrowing the gap, with maximum speeds of up to 7 Mbps in some cases. Wi-Fi hotspots and wireless LANs are also options for wireless Internet connectivity. In these cases, Internet connectivity is typically delivered to a network hub via a wired connection like satellite, cable, DSL or fiber optics and then made available to wireless devices via a wireless access point.

Wireless internet connectivity in cell phones is growing in popularity as well. Cell phones, and other devices featuring windows mobile applications, are now all being designed with advanced wireless technology. This allows them the ability to connect to a wireless broadband internet service, or to the internet via their own cellular phone network. EDGE and EVDO are two of the more popular next-generation mobile system technologies utilized by cellular phone developers.
EDGE (Enhanced Data rates for GSM Evolution) was introduced into the North American via GSM (Global Systems Mobile) networks in 2003 and is now available worldwide. EDGE increases data transmission rates and improves transmission reliability in mobile devices that use it. More importantly, it allows the mobile device to connect to the Internet wirelessly, but its download speed is significantly slower than other mobile wireless technologies. EDGE transmits data at approximately 236.8 kbit/s, which is below the standard for a broadband connection. However, its theoretical maximum speed is 473.6 kbit/s, so it still considered a wireless broadband technology.
E-mail (short for electronic mail ) is the transmission of messages and files via a computer network. E-mail was one of the original services on the Internet, enabling scientists and researchers working on government-sponsored projects to communicate with colleagues at other locations. Today, e-mail is a primary communications method for both personal and business use. You use an e-mail program to create, send, receive, forward, store, print, and delete e-mail messages. Outlook and Windows Live Mail are two popular desktop e-mail programs; Gmail and Windows Live Hotmail are two popular free e-mail Web applications.
The message can be simple text or can include an attachment such as a word processing document, a graphic, an audio clip, or a video clip.An e-mail address is a combination of a user name and a domain name that identifies a user so that he or she can receive Internet e-mail. A user name is a unique combination of characters, such as letters of the alphabet and/or numbers, that identifies a specific user. Your user name must be different from the other user names in the same domain.
A mailing list, also called an e-mail list or distribution list, is a group of e-mail names and addresses given a single name. When a message is sent to a mailing list, every person on the list receives a copy of the message in his or her mailbox. For example, your credit card company may add you to its mailing list in order to send you special offers. To add your e-mail name and address to a mailing list, you subscribe to it.
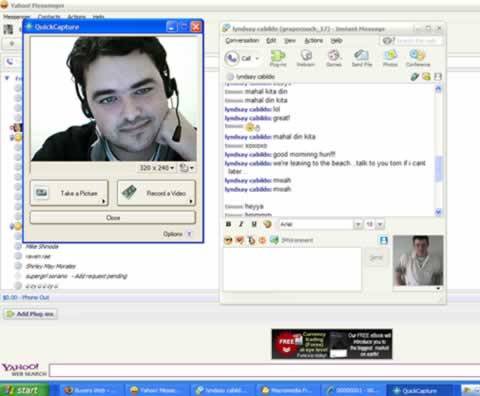
Instant Messaging
Instant messaging (IM) is a real-time Internet communications service that notifies you when one or more people are online and then allows you to exchange messages or files or join a private chat room with them. Real time means that you and the people with whom you are conversing are online at the same time. Some IM services support voice and video conversations (Figure 2-29). Many IM services also can alert you to information such as calendar appointments, stock quotes, weather, or sports scores. They also allow you to send photos.
Chat Rooms
A chat is a real-time typed conversation that takes place on a computer. A chat room is a location on an Internet server that permits users to chat with each other. Anyone in the chat room can participate in the conversation, which usually is specific to a particular topic. As you type on your keyboard, a line of characters and symbols is displayed on the computer screen. Others connected to the same chat room server also see what you have typed. Some chat rooms support voice chats and video chats, in which people hear or see each other as they chat.
Podcasting is similar in nature to RSS, which allows subscribers to subscribe to a set of feeds to view syndicated Web site content. With podcasting however, you have a set of subscriptions that are checked regularly for updates and instead of reading the feeds on your computer screen, you listen to the new content on on your iPod (or like device). The format used for podcasting is RSS 2.0 with enclosures. The podcasting enclosures refer to all binary (non-text) downloads. You can read the text description of the enclosure before downloading the item to view.
Podcasting is a free service that allows Internet users to pull audio files (typically MP3s) from a podcasting Web site to listen to on their computers or personal digital audio players. The term comes from a combination of the words iPod (a personal digital audio player made by Apple) and broadcasting. Even though the term is derived from the iPod, you don't need an iPod to listen to a podcast. You can use virtually any portable media player or your computer.
Webcasting is the method of broadcasting live audio and video in real-time, to audiences all over the world via the Internet. Using streaming media, there is no need to download the content before viewing.
A webcast is a media presentation distributed over the Internet using streaming media technology to distribute a single content source to many simultaneous listeners/viewers. A webcast may either be distributed live or on demand. Essentially, webcasting is “broadcasting” over the Internet.
To use the Internet to broadcast live or delayed audio and/or video transmissions, much like traditional television and radio broadcasts. For example, a university may offer on-line courses in which the instructor Webcasts a pre-recorded or live lecture, or an enterprise may Webcast a press conference in lieu of or in addition to a conference call. Users typically must have the appropriate multimedia application in order to view a Webcast.
In addition to social networking sites, there are other types of sites that help ordinary people communicate across the Web. Many individuals create personal Web sites, called Web logs or blogs, to keep in touch with friends and family. Blog postings are timestamped and arranged with the newest item first. Often, readers of these sites are allowed to comment. Some blogs are like online diaries with personal information; others focus on information about a hobby or theme, such as knitting, electronic devices, or good books. Although most are written by individual bloggers, there are also group blogs with multiple contributors. Some businesses and newspapers also have started blogging as a quick publishing method. Several sites provide tools to create blogs. Two of the most widely used are Blogger and WordPress.
A microblog publishes short sentences that only take a few seconds
to write, rather than long stories or posts like a traditional blog. Microblogs
are designed to keep friends and other contacts up-to-date on
your interests and activities.
The most popular microblogging site,
Twitter, enables you to add new content from your browser, instant
messaging application, or even a mobile phone.
A wiki is a Web site specially designed to allow visitors to fill in missing
information or correct inaccuracies. “Wiki” comes from the Hawaiian
word for fast, which describes the simplicity of editing and publishing
through wiki software.
Wikis support collaborative writing in which there
isn’t a single expert author, but rather a community of interested people
that builds knowledge over time. Perhaps the most famous example is
Wikipedia, an online encyclopedia, written and edited by anyone who
wants to contribute, that has millions of entries in over 20 languages.
Thirteen types of Web sites are portal, news, informational, business/ marketing, blog, wiki, online social network, educational, entertainment, advocacy, Web application, content aggregator, and personal. Many Web sites fall in more than one of these categories.

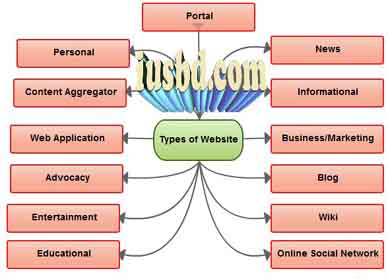
Portal
A portal is a Web site that offers a variety of Internet services from a single, convenient location. Most portals offer these free services: search engine; news; sports and weather; Web publishing; reference tools such as yellow pages, stock quotes, and maps; shopping; and e-mail and other communications services. Many portals have online communities. An online community is a Web site that joins a specific group of people with similar interests or relationships. These communities may offer online photo albums, chat rooms, and other services to facilitate communications among members. Popular portals include AltaVista, AOL, Excite, GO.com, iGoogle, Lycos, MSN, and Yahoo!. A wireless portal is a portal designed for Internet-enabled mobile devices.
News
A news Web site contains newsworthy material including stories and articles relating to current events, life, money, sports, and the weather. Many magazines and newspapers sponsor Web sites that provide summaries of printed articles, as well as articles not included in the printed versions. News papers and television and radio stations are some of the media that maintain news Web sites.
Informational
An informational Web site contains factual information. Other organizations provide information such as public transportation schedules and published research findings.
Business/Marketing
A business/marketing Web site contains content that promotes or sells products or services. Nearly every enterprise has a business/marketing Web site. Allstate Insurance Company, Dell Inc., General Motors Corporation, Kraft Foods Inc., and Walt Disney Company all have business/marketing Web sites. Many of these enterprises also allow you to purchase their products or services online.
Blog
A blog, short for Weblog, is an informal Web site consisting of time-stamped articles, or posts, in a diary or journal format, usually listed in reverse chronological order. A blog that contains video clips is called a video blog, or vlog. A microblog allows users to publish short messages, usually between 100 and 200 characters, for others to read. Twitter is a popular microblog. The term blogosphere refers to the worldwide collection of blogs, and the vlogosphere refers to all vlogs worldwide. Blogs reflect the interests, opinions, and personalities of the author, called the blogger or vlogger (for vlog author), and sometimes site visitors. Blogs have become an important means of worldwide communications. Busi nesses create blogs to communicate with employees, customers, and vendors. Teachers create blogs to collaborate with other teachers and students. Home users create blogs to share aspects of their personal life with family, friends, and others.
Wiki
A wiki is a collaborative Web site that allows users to create, add to, modify, or delete the Web site content via their Web browser. Many wikis are open to modification by the general public. Wikis usually collect recent edits on a Web page so that someone can review them for accuracy. The difference between a wiki and a blog is that users cannot modify original posts made by the blogger. A popular wiki is Wikipedia, a free Web encyclopedia.
Online Social Network
An online social network, also called a social networking Web site, is a Web site that encourages members in its online community to share their interests, ideas, stories, photos, music, and videos with other registered users. Most include chat rooms, newsgroups, and other communications services. Popular social networking Web sites include MySpace and Facebook, with Facebook alone boasting more than 300 million active users. In some social networking Web sites, such as Second Life, users assume an imaginary identity and interact with other users in a role-playing type of environment. A media sharing Web site is a specific type of online social network that enables members to share media such as photos, music, and videos. Flickr, Fotki, and Webshots are popular photo sharing communities; PixelFish and YouTube are popular video sharing communities.
Educational
An educational Web site offers exciting, challenging avenues for formal and informal teaching and learning. On the Web, you can learn how airplanes fly or how to cook a meal. For a more structured learning experience, companies provide online training to employees; and colleges offer online classes and degrees. Instructors often use the Web to enhance classroom teaching by publishing course materials, grades, and other pertinent class information. Entertainment An entertainment Web site offers an interactive and engaging environment. Popular entertainment Web sites offer music, videos, sports, games, ongoing Web episodes, sweepstakes, chat rooms, and more.
Web Application
A Web application, or Web app, is a Web site that allows users to access and interact with software through a Web browser on any computer or device that is connected to the Internet. Some Web applications provide free access to their softwareOthers offer part of their software free and charge for access to more comprehensive features or when a particular action is requested. Examples of Web applications include Google Docs (word processing, spreadsheets, presentations), TurboTax Online (tax preparation), and Windows Live Hotmail (e-mail).
Content Aggregator
A content aggregator is a business that gathers and organizes Web content and then distributes, or feeds, the content to subscribers for free or a fee. Examples of distributed content include news, music, video, and pictures. Subscribers select content in which they are interested. Whenever the selected content changes, it is downloaded automatically (pushed) to the subscriber’s computer or mobile device. RSS 2.0, which stands for Really Simple Syndication, is a specification that some content aggregators use to distribute content to subscribers. Atom is another specification sometimes used by content aggregators to distribute content. Some current browsers include a feature, such as Internet Explorer’s WebSlices, that enables content aggregators to mark sections of their Web pages as feeds to which users can subscribe. Personal A private individual or family not usually associated with any organization may maintain a personal Web site or just a single Web page. People publish personal Web pages for a variety of reasons. Some are job hunting. Others simply want to share life experiences with the world.
A personal firewall is a utility that detects and protects a personal computer from unauthorized intrusions. Personal firewalls constantly monitor all transmissions to and from a computer. When connected to the Internet, your computer is vulnerable to attacks from a hacker. A hacker is someone who tries to access a computer or network illegally. Users with broadband Internet connections, such as through DSL and cable Internet service, are even more susceptible than those with dial-up access because the Internet connection always is on. Operating systems often include a personal firewall. Windows automatically enables its built-in personal firewall, called Windows Firewall, upon installation of the operating system. If your operating system does not include a personal firewall or you want additional protection, you can purchase a stand-alone personal firewall utility or a hardware firewall, which is a device such as a router that has a built-in firewall.
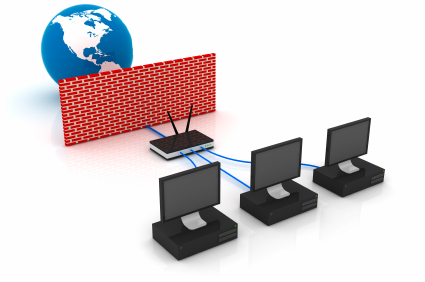
The domain name system (DNS) is the method that the Internet uses to store domain names and their corresponding IP addresses. When you specify a domain name, a DNS server translates the domain name to its associated IP address so that data and information can be routed to the correct computer. A DNS server is an Internet server that usually is associated with an Internet access provider.
aero - Aviation community members
biz - Businesses of all sizes
cat - Catalan cultural community
com - Commercial organizations, businesses, and companies
coop - Business cooperatives such as credit unions and rural electric co-ops
edu - Educational institutions
gov - Government agencies
info - Business organizations or individuals providing general information
jobs - Employment or human resource businesses
mil - Military organizations
mobi - Delivery and management of mobile Internet services
museum - Accredited museums
name - Individuals or families
net - Network providers or commercial companies
org - Nonprofit organizations
pro - Certified professionals such as doctors, lawyers, and accountants
tel - Internet communications
travel - Travel industry
Malware, short for malicious software, is software used or programmed by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of code, scripts, active content, and other software. 'Malware' is a general term used to refer to a variety of forms of hostile or intrusive software.
Malware is short for "malicious software." Malware is any kind of unwanted software that is installed without your adequate consent. Viruses, worms, and Trojan horses are examples of malicious software that are often grouped together and referred to as malware.

There are several free ways to help protect your computer against malware:
Make sure automatic updating is turned on to get all the latest security updates.
Keep your firewall turned on.
Don't open spam email messages or click links on suspicious websites.
Download Microsoft Security Essentials, which is free, or another reputable antivirus and anti-malware program.
Warning: Cybercriminals sometimes try to trick you into downloading rogue (fake) security software that claims to protect you against malware. This rogue security software might ask you to pay for a fake product, install malware on your computer, or steal your personal information.
Install Malware bytes
Spyware is a program placed on a computer without the user’s knowledge that secretly collects information about the user, often related to Web browsing habits. Spyware can enter a computer as a virus or as a result of a user installing a new program. The spyware program communicates information it collects to an outside source while you are online. Adware is a program that displays an online advertisement in a banner or pop-up window on Web pages, e-mail, or other Internet services. Sometimes, spyware is hidden in adware. A spyware remover is a program that detects and deletes spyware and other similar programs. An adware remover is a program that detects and deletes adware. Most spyware and adware removers cost less than $50; some are available on the Web at no cost. Some operating systems and antivirus programs include spyware and adware removers. Popular stand-alone spyware and adware removers include Ad-Aware, Spy Sweeper, Spybot - Search and Destroy, and Windows Defender.
Spyware and Adware Removers Spyware is a program placed on a computer without the user’s knowledge that secretly collects information about the user, often related to Web browsing habits. Spyware can enter a computer as a virus or as a result of a user installing a new program. The spyware program communicates information it collects to an outside source while you are online.

Adware is a program that displays an online advertisement in a banner or pop-up window on Web pages, e-mail, or other Internet services. Sometimes, spyware is hidden in adware. A spyware remover is a program that detects and deletes spyware and other similar programs. An adware remover is a program that detects and deletes adware. Some operating systems and antivirus programs include spyware and adware removers. Popular stand-alone spyware and adware removers include Ad-Aware, Spy Sweeper, Spybot - Search and Destroy, and Windows Defender.
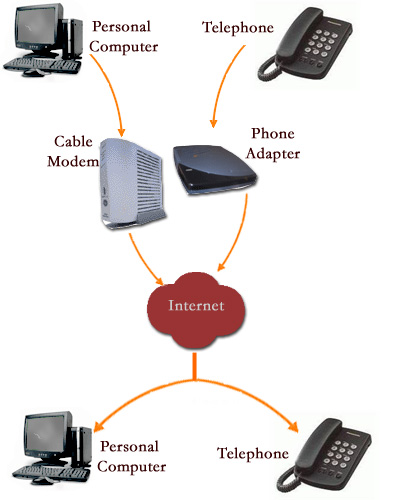
VoIP, (Voice over IP, or Internet Protocol) also called Internet telephony, enables users to speak to other users over the Internet. That is, VoIP uses the Internet (instead of the public switched telephone network) to connect a calling party to one or more local or longdistance called parties. To place an Internet telephone call, you need a high-speed Internet connection (such as a DSL or cable modem); Internet telephone service; a microphone or telephone, depending on the Internet telephone service; and Internet telephone software or a VoIP router, or a telephone adapter, depending on the Internet telephone service. VoIP services also are available on some mobile devices that have wireless Internet service. As you speak in a microphone connected to your computer or a telephone connected to the VoIP router or telephone adapter, the Internet telephone software and the com puter’s sound card or the VoIP router or telephone adapter convert your spoken words (analog signals) to digital signals and then transmit the digitized audio over the Internet to the called parties.
The act of sending an e-mail to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. The e-mail directs the user to visit a Web site where they are asked to update personal information, such as passwords and credit card, social security, and bank account numbers, that the legitimate organization already has. The Web site, however, is bogus and set up only to steal the user's information.

Phishing is a fraudulent attempt, usually made through email, to steal your personal information. The best way to protect yourself from phishing is to learn how to recognize a phish.
Phishing emails usually appear to come from a well-known organization and ask for your personal information — such as credit card number, social security number, account number or password. Often times phishing attempts appear to come from sites, services and companies with which you do not even have an account.
In order for Internet criminals to successfully "phish" your personal information, they must get you to go from an email to a website. Phishing emails will almost always tell you to click a link that takes you to a site where your personal information is requested. Legitimate organizations would never request this information of you via email.
Online banking (or Internet banking or E-banking) allows customers of a financial institution to conduct financial transactions on a secure website operated by the institution, which can be a retail or virtual bank, credit union or building society.
To access online banking, the customer would go to the financial institution's website, and enter the online banking facility using the customer number and password. Some financial institutions have set up additional security steps for access, but there is no consistency to the approach adopted.

You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the cloud? Basically, the cloud is the internet - more specifically, it's all of the things that you can access remotely over the internet. When something is in the cloud, that means it is stored on servers on the internet, instead of on your computer. It lets you access your calendar, email, files and more, from any computer that has an internet connection.
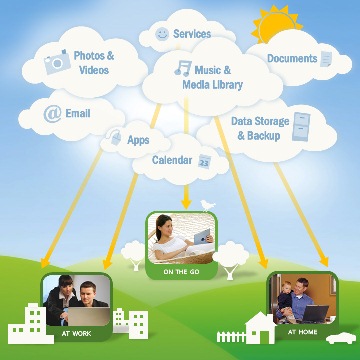
If you've ever used web-based email, then you've used the cloud - all of the emails in your Inbox are stored on servers. However, there are many other services that use the cloud in different ways. Here are just a few examples:
Why use the cloud?
There are many reasons to use the cloud, but the main reasons are convenience and reliability. In the past, if you wanted to bring a file with you, you would have to save it to a USB flash drive, external hard drive, or CD-R disc. Saving a file to the cloud ensures that you'll be able to access it with any computer that has an internet connection, so you don't have any physical media to keep track of. The cloud also makes it much easier to share a file with coworkers or friends, making it possible to collaborate over the internet.
With the cloud, you're much less likely to lose your data, since it is stored on servers. However, just like anything online, there is always a risk that someone may try to gain access to your personal data, so it's important to choose a strong password and pay attention to any privacy settings for the service you're using.
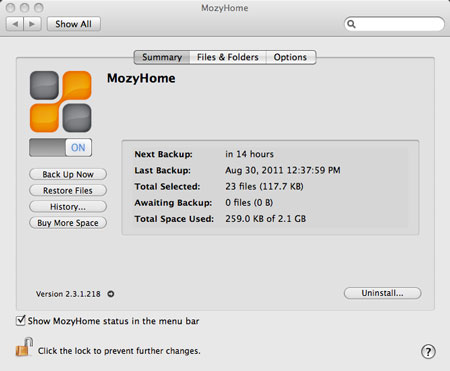
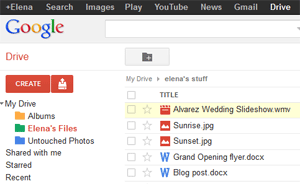
What is a web app?
Previously, we talked about how desktop applications allow you to perform tasks on your computer. However, there are also web applications (or web apps), which run in the cloud and do not need to be installed on your computer. These are sometimes called cloud apps.
Web apps are becoming more and more integrated with websites, and it may be hard to distinguish between a web application and a "regular" website. In many cases, you may be using a web application without even knowing it!
When you use a web app, you are working from your computer or mobile device, but much of the actual processing is done by a network of servers. These servers can pool all of their processing power in order to handle requests from all over the world. They also use specialized servers to store the data that you're working with, as well as the data from all of the other users. All of this happens very seamlessly, so it looks almost like the application is running on your computer.
For example, if you open a document with Google Docs, your web browser will communicate with the network of servers to display your document. As you edit the document, your browser will work closely with the servers to make sure everything is kept up-to-date.
What Is Cloud Storage, and What Are Its Advantages? Cloud storage is an Internet service that provides storage for computer users. Available for all sizes of users, with various degrees of storage services available for home and business users, cloud storage fees vary, depending on the user’s storage requirements. Advantages include accessing fi les on the Internet from any computer or device with Internet access; storing large audio, video, and graphics fi les on the Internet instantaneously; allowing others to access their fi les on the Internet; viewing time-critical data and images immediately; storing off-site backups of data; and providing data center functions.
What is uncapped?
The broadband terms capped, uncapped and unlimited have caused heated debates in the past, and to try to clarify these terms ISPA divided broadband services into four categories.
Capped ADSL means that once your monthly bandwidth allocation is used up, your connectivity will drop to a speed which essentially makes it unusable for Interenet use. In most cases capped ADSL solutions have a soft and a hard cap. This means that once your data bundle is exceeded you are still allowed to surf locally with International bandwidth dropping to an unusable rate. Once you double the usage locally a hard cap kicks in and your local bandwidht drops to an unusable rate too.
This type of ADSL solution is ideal if you have a fixed monthly budget and want to make sure you don't get an ADSL bill that varies each month. In todays tough times this is quiet a popular choice, especially for parents who want to provide their children with access but avoid any damages to the monthly budget. This is especially relevant for parents whose tech-savy kids demand Interenet Access but they themselves hardly use it.
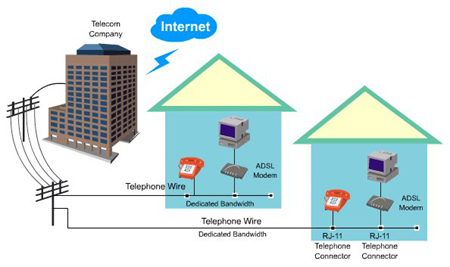
Uncapped ADSL comes in two forms namely consumer uncapped ADSL and business uncapped ADSL.
A consumer uncapped ADSL offering means that once your purchased data bundle has been used up for the month you can continue to use the Internet but you are charged for each megabyte over your allocated bandwidth that you use. This is some-times referred to as soft capping. In this case your ADSL line speed does not impact the cost of the account as the more you use the more you pay.
There second type of uncapped ADSL is a uncapped ADSL solution at a fixed prices each month. The "catch" here is that your line speed is limited to a maximum amount depending on the contract you buy. The higher you line speed, 512Kbps ADSL, 1Mbs ADSL the higher the monthly cost. The monthly fixed cost is also relatively high and this ADSL offering is aimed as SMEs or home offices. It allows SMEs to easily budget for ADSL usage as a fixed monthly cost.
Although the first option is referred to as a "consumer" offering it is often used by businesseses, because of its lower costs, who can accuratly plan their usual monthly usage but occassionally exceed their cap. Since it is uncapped businesses can continue to use the Internet since the cost of being without ADSL access outweighs the cost per megabyte that you pay. In the long run using such an offering is cheaper than using the uncapped business ADSL solution if you manage the monthly usage appropriately and make adjustments when necessary. Usually if overusage continues for some months the business will upgrade their package to a higher but cheaper overall package.
Anti-Spam Programs Spam is an unsolicited
e-mail message or newsgroup posting sent to many
recipients or newsgroups at once. Spam is Internet
junk mail. The content of spam ranges from selling
a product or service, to promoting a business
opportunity, to advertising offensive material. An
anti-spam program is a filtering program that
attempts to remove spam before it reaches your
inbox. If your e-mail program does not filter spam,
many anti-spam programs are available at no cost
on the Web. Internet access providers often filter
spam as a service for their subscribers.
Pop-Up Blockers A pop-up ad is an Internet
advertisement that suddenly appears in a new window
in the foreground of a Web page displayed
in your browser. A pop-up blocker is a filtering
program that stops pop-up ads from displaying on
Web pages. Many Web browsers include a pop-up
blocker. You also can download pop-up blockers
from the Web at no cost.
Intranets Recognizing the efficiency and power of the Internet, many organizations apply Internet and Web technologies to their internal networks. An intranet (intra means within) is an internal network that uses Internet technologies. Intranets generally make company information accessible to employees and facilitate working in groups. Simple intranet applications include electronic publishing of organizational materials such as telephone directories, event calendars, procedure manuals, employee benefits information, and job postings. Additionally, an intranet typically includes a connection to the Internet. More sophisticated uses of intranets include groupware applications such as project management, chat rooms, group scheduling, and video conferencing. An intranet essentially is a small version of the Internet that exists within an organization. It has a Web server, supports Web pages containing multimedia, and is accessible via a Web browser such as Internet Explorer, Firefox, Opera, Safari, and Google Chrome. Users update information on the intranet by creating and posting a Web page, using a method similar to that used on the Internet .
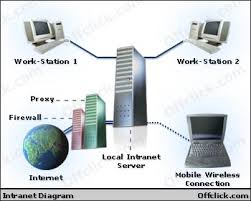
FTP (File Transfer Protocol ) is an Internet standard that permits file uploading and downloading with other computers on the Internet. Uploading is the opposite of down loading; that is, uploading is the process of transferring documents, graphics, and other objects from your computer to a server on the Internet. Web page authors, for example, often use FTP to upload their Web pages to a Web server. Many operating systems include FTP capabilities. If yours does not, you can download FTP programs from the Web, usually for a small fee. An FTP server is a computer that allows users to upload and/or download files using FTP. An FTP site is a collection of files including text, graphics, audio clips, video clips, and program files that reside on an FTP server. Many FTP sites have anonymous FTP, whereby anyone can transfer some, if not all, available files. Some FTP sites restrict file transfers to those who have authorized accounts (user names and passwords) on the FTP server.
ICT has changed the way we work in many different ways such as instant transfer of information and making organisations more efficient by cutting down the time it takes to transfer information. ICT has changed the employment structure and working practices. This is by having more storage space because everything saved is stored onto computers and hard drives. Computers are able to process information for you without you manually needing to calculate things such as wages. Some people decide to work from home and they’re work can be saves on USB sticks so files can be moves from computer to computer. This also means that you can work from wherever there is a computer available. Also companies are better as they have the resources to create advertisements and flyers so there workplace is known better.
IT and Society
Understand how computers can simplify our work practices
Office automation |
The computer has totally revolutionized the modern office. This goes far beyond simply replacing the typewriter with a computer. A computer can be linked to other computers. The computer can be linked to the telephone system. The fax machine is fast being replaced in many companies where faxes are sent and received directly via the computer, or replaced entirely by email! Software producers’ aim is to create a paperless office. |
Home working (Teleworking) |
It can be defined as working at home using electronic communications. With the advent of modern telecommunications and the right software, it is now possible for many people to work at home on a computer that is connected to the office. This has a huge advantage to the companies using these home workers. The company doesn’t have the overhead of office space and equipment. Many employees find it much more convenient to work from home. Some companies are now extending this idea and using employees living in other countries. |
Email is very efficient because, unlike letters that are sent via the post, an email message or file is received almost immediately it is sent. A single email can simultaneously be send to many different people. This can be very useful in a business environment. However, this facility can be abused. It is possible for people to send email via the Internet to millions of people (junk mail). This is known as Spamming by the Internet community, and is very strongly disapproved of! |
|
Electronic commerce |
Definition: The buying of services and goods and paying for them on-line. Major software companies are totally revamping their products to make them Internet-enabled. Banks have to rethink their strategy of targeting and servicing their customers by providing online banking. Businesses are establishing a presence on the Web to offer products and services electronically. |
Smart card |
Special plastic card containing a processor and memory. It is used to pay for goods and services. Each time the card is used the details on the card (e.g. bank balance) are updated. |
CAM |
Computer-Aided Manufacturing – The use of computers to control production processes; in particular, the control of machine tools and robots in factories. In some factories, the whole design and production system has been automated by linking |
Understand how computers can affect people’s health
|
Using a computer can cause the following: repetitive strain injury (RSI), sore and itchy eyes, back problems. |
Repetitive Strain injury (RSI) |
Inflammation of tendon sheaths, mainly in the hands and wrists, which may be disabling. It is found predominantly in factory workers involved in constant repetitive movements, and in those who work continually with a computer keyboard and mouse. The symptoms include aching muscles, weak wrists, tingling fingers and in severe cases, pain and paralysis. What to look out for:
|
Eye-strain |
|
Lighting |
Adequate lighting is important to create a good working environment. Lights should not point at computer screens. |
Awareness of the importance of technical security:
Passwords |
The main purpose of a password in a computer system is to ensure that only authorised or registered people use the computer system. Install password protection to prevent intruders from accessing your computer, and accessing the files stored on your computer. |
Definition |
Backing up means making an electronic copy of the data. |
Why backup? |
The most important thing that you store on your computer is information. The contents of a hard disk can represent years of work. If the hard disk stops working one day, you could lose all those information. It is therefore vital that you make regular backups of the information stored on the computer. |
Organise your data efficiently |
Your computer contains many programs, and also a large amount of data that you have created. It is only the data that really needs to be backed up. If you create a folder that contains only data, only this directory (plus any sub-directories) needs to be backed up. |
System backup vs. Incremental backup |
A system backup means that you backup all the data on your computer. This has the advantage that the entire hard disk can be backed up, but suffers from the disadvantage that this process can take a long time if your computer contains a lot of data. |
Off-site Storage |
Security backup data should be stored in a physically different location from the original data. It is no good backing up your data, only to leave the disks or tapes next to the computer. If someone steals your computer it is likely that they will also steal your backups! If you have a fire you will also lose your backups if they are stored in the same office or building. |
Maximum protection |
The best possible security protection is achieved by making a system backup every day, stored both on-site and off-site. |
Beware of 'open files' |
You should perform backups at night. If you backup your computer during the day (when you are using programs on the computer) then any program or data files that are in use at the time of the backup will not be backed up. The backup program will skip these “open” files. |
Virus definition |
It is a program designed to replicate itself, often with the aim of disrupting a computer system. A computer virus affects the operation of a computer. Different viruses are activated in different ways. Some are activated on a specific date. BEWARE: Viruses can destroy all your data! Viruses most commonly infect disk partitions and files |
Anti-virus software |
Unless you use virus detection software, the first time that you will know that you have a virus, is when it activates, because computer viruses are spread unknowingly. Anti-virus software can prevent programs or data being altered by a malicious program. |
Macro virus |
A macro virus is a virus that can be hidden in some word processing documents. In word processors like Word or Word Power, a macro is a series of commands and instructions that you group together as a single command to accomplish a task automatically. These macros form part of a document. When such an infected document is send as an email message to you, the virus is spread with it, and it will affect all similar documents on your computer. |
How do viruses infect PCs? |
Viruses hide on a disk, and when you access the disk (either a diskette or another hard disk over a network) the virus program will start and infect your computer. The worst thing about a computer virus is that they can spread from one computer to another, either via use of infected floppy disks, or over a computer network. |
How to prevent virus damage |
The best way to minimise the spread of computer viruses is by always checking shared files or software. There are a number of third party anti-virus products available. The main thing about your virus checker is that it should be kept up to date. Many companies supply updated disks on a regular basis or allow you to receive updates through an electronic, on-line bulletin board. |
Make a diskette read-only |
If you are using 3 1/2" diskette, there is a notch that can be opened or closed which may be used to protect the disk (you cannot change data on the disk). A virus cannot be transmitted onto a write-protected floppy disk. |
If PC is infected – what to do? |
The best course of action if you suspect that a PC has a virus, is to shut down and reboot from a clean floppy boot disk, and then run a virus-checking program. |
Freeware |
Some software is made freely available. Demonstration disks often come under this category. Also a lot of software is produced by the educational community and is made available for free. You can thus legally copy it without a license. Always read any licenses supplied with such software very carefully before using it. |
Shareware |
Shareware is software that is freely available and is designed to let you use the product for free, for a limited period while you decide if you like it or not. After this period you must legally either remove it, or pay an amount to the producers of the product. |
Beta software |
Pre-release version of a new software program that is still under development. It is handed out to users for testing. Beta testers use the software to do real work and report any bugs or badly implemented features they find to the developers, who incorporate this information in refining the product for release. |
Single User License |
A single-user license implies that only one concurrent user may operate the program at a time. This is the license you get when you buy a software application for personal use. |
Site License (Multi-user License) |
Many large companies do not go out and physically buy a certain amount of copies of each software product that they need. Instead they will buy a site license. Generally this means that the company purchasing the license can make a fixed numbers of copies (like 20 or 30) available to their staff, normally via a company network. |
Data protection and privacy issues
|
The main reason for computer security is the safety of business data. You also have a moral and legal duty to treat information about individuals with respect and keep it confidential. Confidentiality is a way of keeping sensitive and personal information private. |
Data encryption |
Sometimes, data is scrambled (put into a secret code) to make it unreadable, except by authorized users. This is called encryption. |
Hacking |
Computer hacking is the attempt to overcome security and gain access to information. |
What is a Firewall ? |
A “Firewall” stops unauthorised access into a network. |
Purpose |
To protect the privacy of the individual by controlling the data about individual people which is stored on computer systems. |
Regulates data |
The Council of Europe adopted, in 1981, a Data Protection Convention, which led in the UK to the Data Protection Act 1984. This requires computer databases containing personal information to be:
|
Misuse of data |
If an individual opens an account at e.g. a clothing store, the clothing store will require the individual to supply a certain amount of personal information. The clothing store may not cross-reference the data with a different organisation. |
Social Networking
Social Networking
One of the fastest-growing uses of the Internet is social networking, or connecting
individuals to one another. While many social networking sites support
a wide range of activities, there are three broad categories: reuniting,
friend-of-a-friend, and common interest.
• Reuniting sites are designed to connect people who have known one
another but have lost touch; for example, an old high school friend that
you have not seen for several years. You join a social network by connecting
to a reuniting site and providing profile information such as your age,
gender, name of high school, and so forth. This information is added to the
reuniting site’s member database. Members are able to search the database
to locate individuals. Many of the sites will even notify you whenever a
new individual joins that matches some parts of your profile (such as high
school class). Two of the best-know reuniting sites are Classmates Online
and Facebook.
• Friend-of-a-friend sites are designed to bring together two people who
do not know one another but share a common friend. The theory is that,
if you share a common friend, then it is likely that you would become
friends. For example, a network could be started by one of your acquaintances
by providing profile information on him- or herself and a list of
friends. You could visit your acquaintance’s site to connect to a friend(s) of
your acquaintance. You could even join the list of friends provided at the
site. Two well-known friend-of-a-friend sites are Friendster and MySpace.
• Common interest sites bring together individuals that share common
interests or hobbies. You select a networking site based on a particular
interest. For example, if you wanted to share images, you might join
Flickr or YouTube. If you are looking for business contacts, you might
join Linkedln. If you wanted to locate or create a special interest group,
you might join Meetup.
Genesis Design